Iespējams, ka saistībā ar neseno slavenību kailfoto nopludināšanu internetos, kas tika sasaistīta ar Apple iCloud, ir pastiprināta interese par drošību Apple ierīcēs un servisos. Šodien pamanīju Hacker News saiti uz Apple iOS sistēmas drošības dokumentāciju (PDF).
Labā ziņa, ka šajā dokumentā bija dažas ilustrācijas par procesiem, kas tur notiek, sliktā, ka to bija pārāk maz, lai izveidotu galeriju. Principā dokuments ir garlaicīgs un satur daudz teksta – var noderēt reizēs, kad nenāk miegs. 🙂
Bet arī no šāda garlaicīga dokumenta, var izkasīt šo to interesantu un plašākai publikai baudāmu informāciju. Kaut kādus pamatprincipus tam kā tiek glabāti faili iOS ierīcēs.
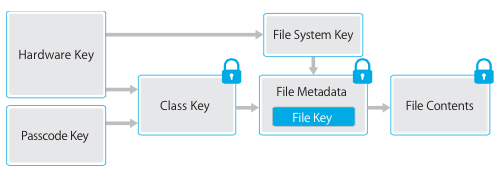
File Data Protection
In addition to the hardware encryption features built into iOS devices, Apple uses a technology called Data Protection to further protect data stored in flash memory on the device. Data Protection allows the device to respond to common events such as incoming phone calls, but also enables a high level of encryption for user data. Key system apps, such as Messages, Mail, Calendar, Contacts, and Photos use Data Protection by default, and third-party apps installed on iOS 7 or later receive this protection automatically.
Data Protection is implemented by constructing and managing a hierarchy of keys, and builds on the hardware encryption technologies built into each iOS device. Data Protection is controlled on a per-file basis by assigning each file to a class; accessibility is determined by whether the class keys have been unlocked.
Vai arī to kādā veidā tiek sūtīti ziņojumi caur Apple iMessage servisu.
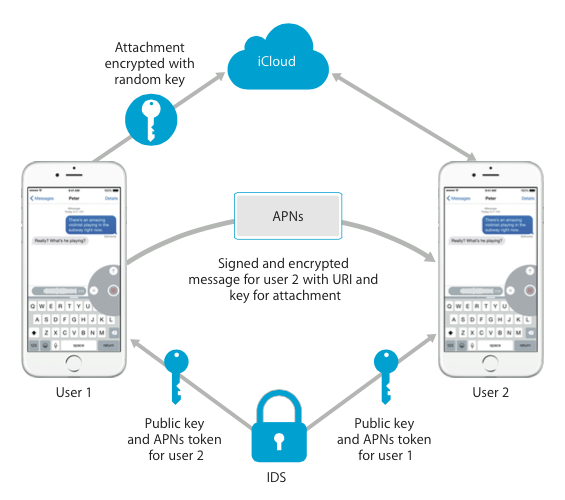
Apple aplikāciju datu aizsardzības principi.
Data Protection in apps
The iOS Software Development Kit (SDK) offers a full suite of APIs that make it easy for third-party and in-house developers to adopt Data Protection and help ensure the highest level of protection in their apps. Data Protection is available for file and database APIs, including NSFileManager, CoreData, NSData, and SQLite.
The Mail app (including attachments), managed books, app launch images, and location data are also stored encrypted with keys protected by the user’s passcode on their device. Calendar (excluding attachments), Contacts, Reminders, Notes, Messages, Photos, and Health ancillary data implement Protected Until First User Authentication.
User-installed apps that do not opt-in to a specific Data Protection class receive Protected Until First User Authentication by default.
Pēdējā Apple produktu prezentācija, kurā tika prezentēts jaunais pakalpojums Apple Pay, raisīja aktīvas diskusijas. Galvenais iemesls ir tas, ka nav īsti skaidrs kā Apple piedāvātais risinājums, kas nav pārāk inovatīvs, spēs nodrošināt tos solījumus, kurus mēs saklausījām.
Maģiskā daļa, kas nodrošina Apple klienta autentifikācija tiek panākta ar jaunā iPhone lietotāja pirkstu nospiedumu, kuru atpazīst Touch ID sistēma.
Touch ID
Touch ID is the fingerprint sensing system that makes secure access to the device faster and easier. This technology reads fingerprint data from any angle and learns more about a user’s fingerprint over time, with the sensor continuing to expand the fingerprint map as additional overlapping nodes are identified with each use.
Touch ID makes using a longer, more complex passcode far more practical because users won’t have to enter it as frequently. Touch ID also overcomes the inconvenience of a passcode-based lock, not by replacing it but by securely providing access to the device within thoughtful boundaries and time constraints.
Touch ID sistēmas uzdevums ir nodrošināt Apple Pay pakalpojuma uzvaras gājienu vai arī tīri pretēji – sakāvi. Šobrīd ir vēl joprojām daudz neskaidrību par to, kas un cik daudz riskus uzņemsies, bet to mēs redzēsim, kad sistēma sāks strādāt.
Mani piesaistīta Touch ID sistēmas rezerves risinājuma darbības princips. Tie ir tie gadījumi, kad pirkstu lasītāja vietā tiks izmantots PIN kods, jo, piemēram, lasītājs nespēj atpazīt saimnieku, bet viņu vajag atpazīt.
Touch ID and passcodes
To use Touch ID, users must set up their device so that a passcode is required to unlock it. When Touch ID scans and recognizes an enrolled fingerprint, the device unlocks without asking for the device passcode. The passcode can always be used instead of Touch ID, and it’s still required under the following circumstances:
- The device has just been turned on or restarted.
- The device has not been unlocked for more than 48 hours.
- After five unsuccessful attempts to match a fingerprint.
- When setting up or enrolling new fingers with Touch ID.
- The device has received a remote lock command.
When Touch ID is enabled, the device immediately locks when the Sleep/Wake button is pressed. With passcode-only security, many users set an unlocking grace period to avoid having to enter a passcode each time the device is used. With Touch ID, the device locks every time it goes to sleep, and requires a fingerprint—or optionally the passcode—at e!very wake.
Vairāk garlaicīgi teksti ir atrodami pašā dokumentā.